¶ Using the QRadar Console
Below are the basic instructions to use the QRadar Console. To access the console, make sure you are connected to the Secure ISS SOC Network via a VPN using Palo Alto’s Global Protect VPN client.
For instructions on setting this up, please read the Setup Guide Q Radar VPN Access.
¶ Logging In and Navigating Around
- Once connected to the VPN and you have gone to https://qradar.secure-iss.com/console/logon.jsp with your browser, you will need to logon to the Console.
- Once logged in, you will be presented with the Main Console Window. The Menu Items available are located across the top of the window and by default, the Dashboard is selected.
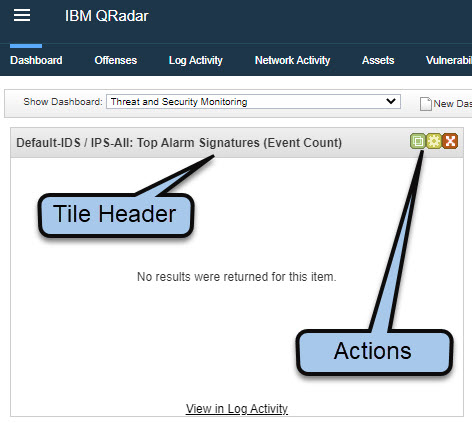
- The Main Console Window default view can be customised by removing or rearranging the tiles to your preferred look. To move a tile, click on the Tile Header and drag into the desired area. To perform other actions like Remove or Change Setting, click on of the Icons in the Actions Area.
¶ Diving in a Little Deeper
The Dashboard View provides a nice birds-eye summary of the network, but you can drill down further by selecting one of the other menu items such as Offenses. From this perspective, the view is more granular, in this case to Offenses. An Offense is simply a collection of events that QRadar has grouped together due to some commonality.
Note: An Offense does not necessarily mean the network is under attack. It is simply the term used by QRadar for a group of events with some common elements. Other SIEM systems may refer to an Offense as an Alert.
The Section below explains how to drill-down into the items. We will use the Offenses menu for this example, but the other menu items operate in a similar way.
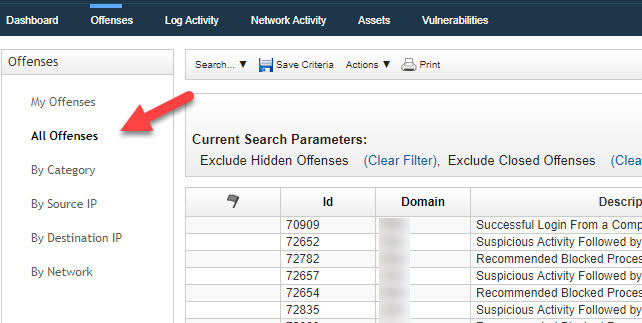
- The Menu on the left provides some simple filters out of the box. By default, All Offenses are listed in the Main Window but can be filtered by clicking on of the simple filter options.
Note: When conducting a Search or applying a Filter, QRadar is asked to perform a computational task on what can sometimes be a large amount of data. Be patient. It can time many seconds or longer to display the result.
¶ Conducting a Search
A quick way to conduct a search is to use the Quick Search function.
- Select the Menu item for the search you want to use (in this example, Log Activity) and click the Quick Search sub-menu. A dropdown will display all the pre-configured Quick Searches from which you can choose.
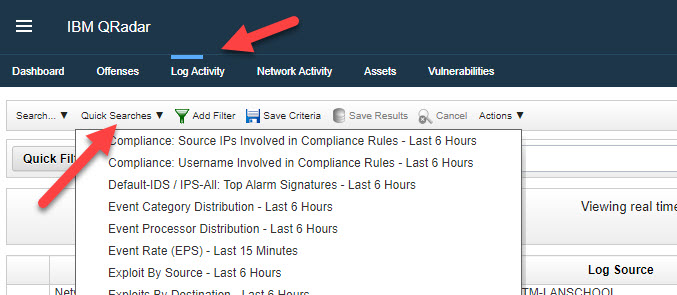
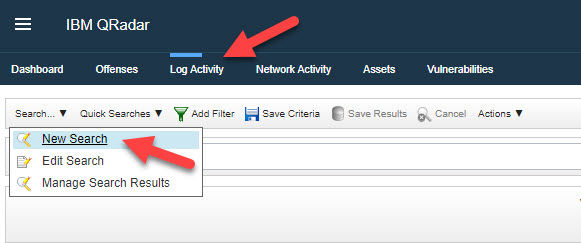
- Alternatively, you can conduct a specific search by using the Search Sub Menu and selecting New Search. This will open the Search parameters in the main window, and this can be quite detailed with many options. Try scrolling down to the Search Parameters section and select the parameter you wish to investigate, in this example, Log Source (indexed).
- Once selected, you can narrow down the parameter using the other options, in this example, narrowing down to a specific server.
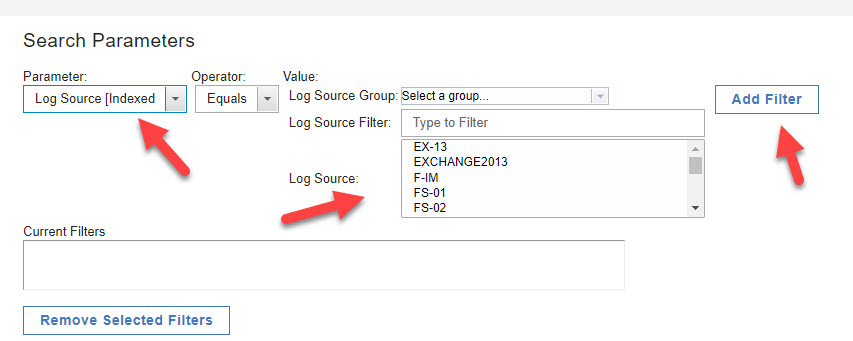
- Click Add to add the filter and then click search in the lower right corner.
Note: When conducting a Search it is good practice to narrow your parameter selection to one that is Indexed, as in the example provided. Indexed items are searchable much more efficiently in QRadar and can provide results much quicker.
¶ Further Research
If using the QRadar Console is something of interest and you wish to dive deeper, there are some great resources online. Try the YouTube channel of Jose Bravo found here. https://www.youtube.com/c/jbravovideos/videos