¶ Palo Alto Blacklist/EDL Ingestion
The Secure-ISS QRadar Blacklist allows the Secure-ISS SOC Team to quickly and independently remediate threats, utilising the Palo Alto Firewall’s ‘External Dynamic List’ feature to frequently poll our both automatically and manually populated blacklist. Allowing the SOC Team to remediate via blacklisting a malicious IP address in less than 5 minutes without intervention from your team.
Implementing this functionality will consist of configuring an External Dynamic List (EDL) object and including the Object in a pair of rules to deny the traffic on both the Inbound and Outbound directions. If you already have rules to leverage the built-in Palo Alto published EDLs (and we do recommend doing so) you may simply add this new EDL Object to your existing rule (if you’re not already utilising these EDLs it will be simple to start doing so at the same time)
For more information about EDLs and the Built-in Palo Alto EDLs please see the Palo Alto Documentation
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/external-dynamic-list.html
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/built-in-edls.html
¶ Admission Criteria and Safety
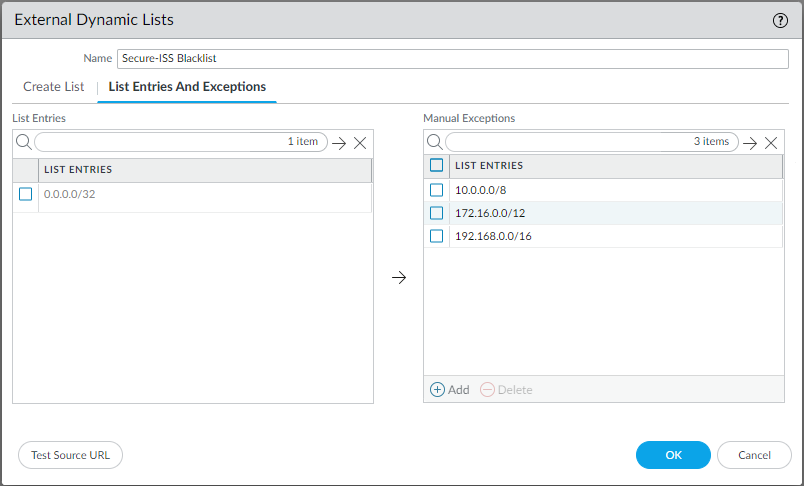
We have excluded/whitelisted the 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 networks from appearing on this list.
An address will only be added to this list as part of a automatic process if it is observed performing specific behaviours directly by the Secure-ISS QRadar Console across our client networks, currently we do not automate admissions of Australian IP addresses to minimise risk of service impacts, as the vast majority of malicious reconnaissance traffic is of foreign origin this significantly reduces the need for manual review, reducing remediation time. Australian IP addresses may still be included on this list by manual means after analyst review.
In keeping with multiple layers of risk mitigation, we are excluding/whitelisting any IP addresses disclosed to us, as part of the onboarding process, from appearing on this list via automated means regardless of the country of origin detected. As it is possible this information may be incomplete/incorrect we do recommend updating us with a current list of Public IP addresses in use, and as an additional redundant layer of protection manually whitelisting these addresses and the local IP address ranges in step 2c of the EDL Setup (below).
¶ Setup
These instructions will be a contextualised walkthrough of the official Palo Alto Documentation, if you would like to follow the Palo Alto documentation yourself directly please see Configure the Firewall to Access an External Dynamic List and Enforce Policy on an External Dynamic List.
¶ Configuring the EDL
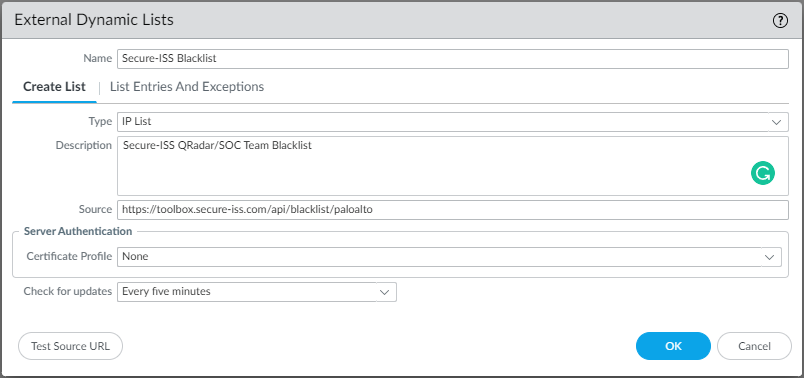
- Navigate to ‘Objects > External Dynamic Lists’ in your Palo Alto Firewall.
- Add a new EDL Object of IP type(Default), called ‘Secure-ISS Blacklist’ (Or similar)
2a. Configure the source to be https://toolbox.secure-iss.com/api/blacklist/paloalto
2b. Configure the ‘Check for Update’ interval to 5 minutes for optimal responsiveness.
2c. (optional/recommended). On the ‘List Entries and Exceptions’, add any Public IP addresses in use or of known trusted management access, and any local IP address scopes for redundant risk mitigation as detailed above. - If you wish to use certificate verification please follow the Palo Alto Documentation to do so.
- Test the Source URL, if the URL is not retrieved you may need to configure the interface used to retrieve EDLs as defined in the Service Routing Configuration ( Device > Setup > Services > Service Route Configuration > Customize - External Dynamic Lists) to an external interface. (Note: The built-in EDLs do not use this configuration and will not be affected by these changes)
- Save/Confirm the new object. (Note if you Commit at this point and attempt to verify if the EDL is being populated, please note that that EDLs are not actively polled until they are referenced in a policy)
¶ Configuring a Policy to use an EDL
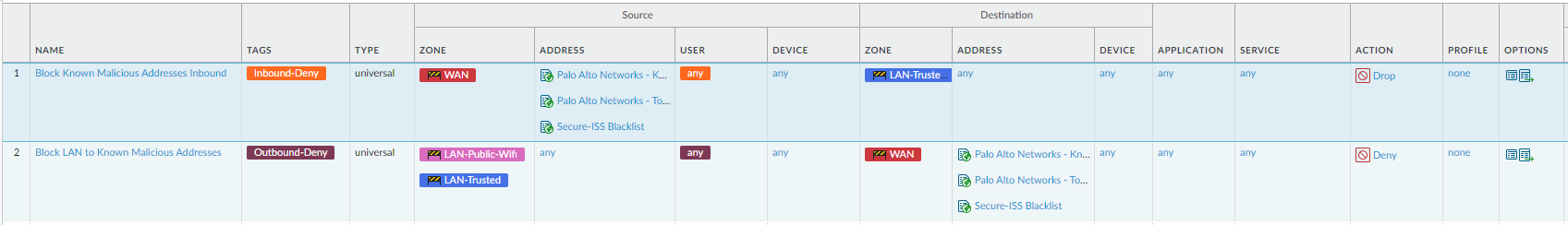
The EDL can be included in Security Policies similar to any other type of address object.
Setup two rules, one to block inbound traffic and another to block outbound traffic including the ‘Secure-ISS Blacklist’ EDL address object in the Source and Destination respectively. The outbound rule is important to block reverse shell traffic, malicious payload hosts and so shouldn’t be overlooked.
As previously mentioned we do recommend utilising the inbuilt Palo Alto EDLs, which can share the same rules as pictured.
The rules should be positioned at the very top of your security policies (but below any anti-lockout policies that you may have in place.)
Whether you wish to drop or block the traffic is up to you, in the example below we are silently dropping inbound connections but acknowledging with a deny for outbound traffic.
Direct Link to image
Don’t forget to commit your changes.
¶ Testing the Blacklist
Once the Dynamic Blacklist has been configured., it is possible to test the Blacklist Ingestion.
Secure-ISS SOC has added a harmless URL/IP to the Blacklist that can be used as a test.
From a workstation that resides in a Zone to which the Blacklist Security Policies apply, open a browser and go to https://www.thelocal.dk/ (34.107.176.5)
If the Blacklist is being successfully ingested, you should not be able to get to the Website.