¶ Microsoft PKI Monitoring
Monitoring of Certificate Authority events and activities is vital to ensure that any compromise of this infrastructure can be detected in a timely and effective manner.
These style of attacks are often seen within Penetration testing activities and real world attacks.
¶ Configuring Certificate Authority Auditing
By default, a number of events will not be generated or logged and in turn can’t be collected by a SIEM solution nor correlated to detect anomalous or malicisous activities.
To ensure effective visibility, this article will walk through turning on the Certificate Authority Auditing.
¶ Microsoft Windows Audit Policy
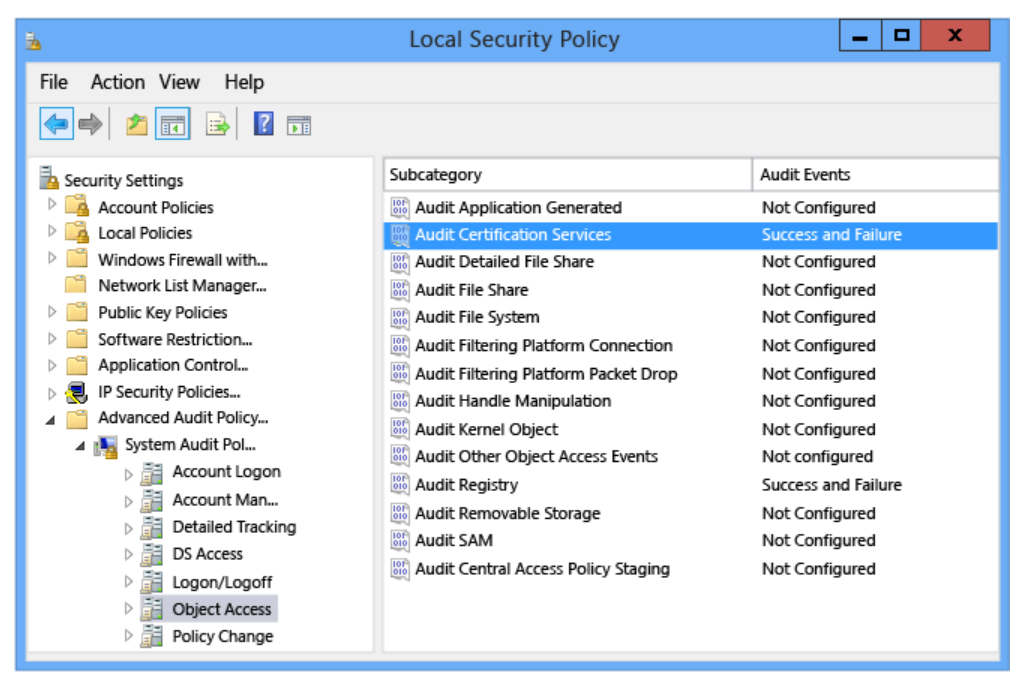
As an initial step we need to ensure that the Windows Audit Policy is configured correctly (on all in-scope CA Servers). Specifically we need to ensure that the "Audit Certification Services” subcategory is configured for success and failure on the in-scope CA Servers.
This can be configured via Group Policy or the command line.
¶ Single Server/ local policy change
For environments within a single server or a non-domain joined server, this can be completed via the command line (Administrator prompt) as follows:
auditpol /set /subcategory:"Certification Services" /success:enable /failure:enable
¶ Group Policy
Our preferred option is to apply a group policy to the in-scope CA servers within an environment.
To set an audit policy using group policies, configure the “Certification Services” subcategory under Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy. Set the subcategory to be enabled for “Success and Failure”.
More information can be found on Microsoft’s official pages.
¶ Confirming enforcement - Settings
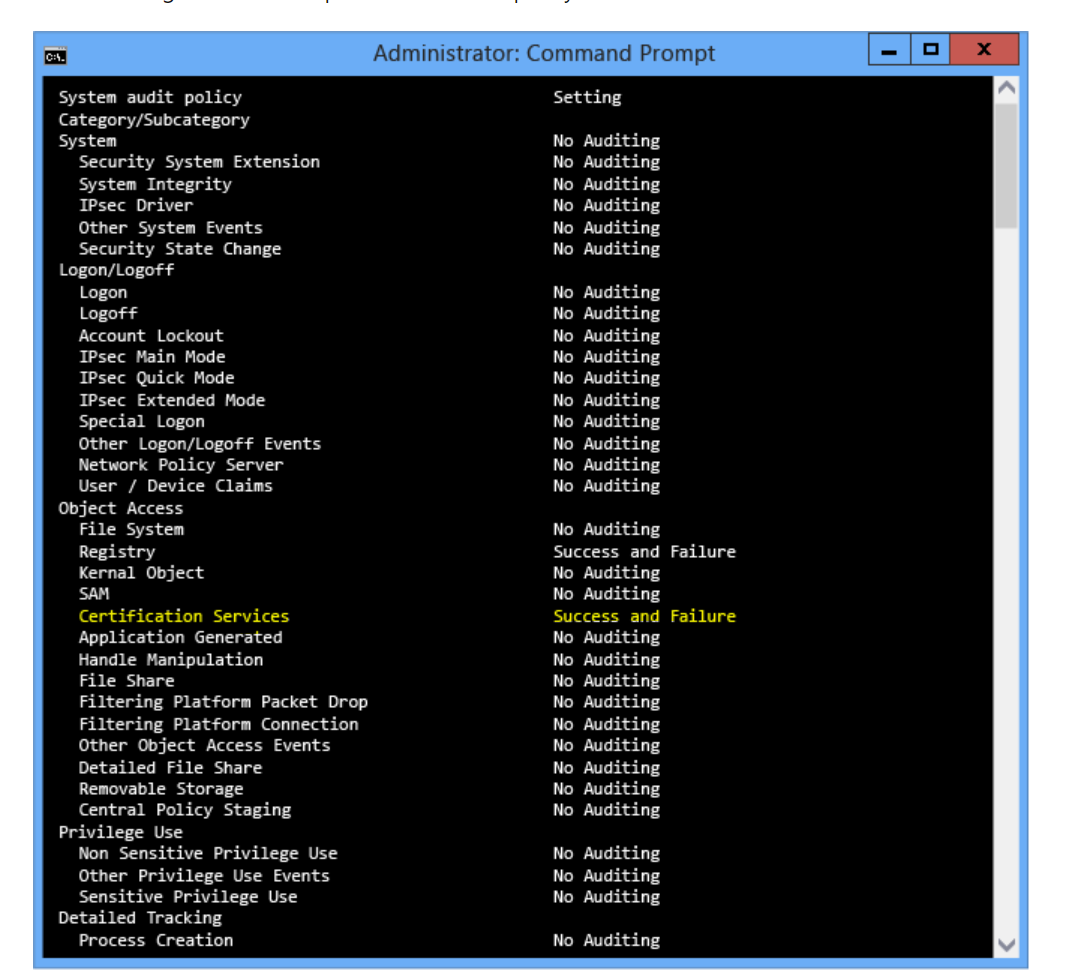
To confirm that the policy change has been successful, run the following on the target CA servers:
auditpol /get /category:*
You should be able to the policy as highlighted in yellow below.
¶ Certificate Authority Auditing
Once the Audit policy has been established, we now need to ensure that the CA “Auditing” Properties are configured correctly. The following will need to occur on all CA servers in the fleet.
Run the Certificate Authority application (or access via the MMC Snap “certsrv”).
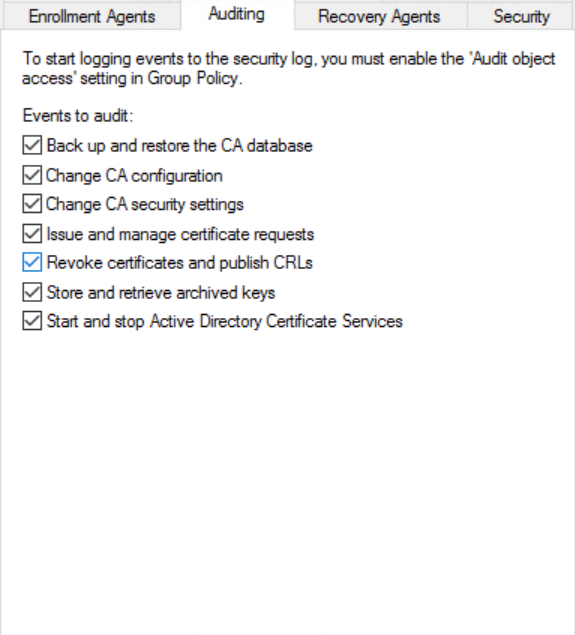
Right click on your CA Server and select “Properties”, and then go to the Auditing tab. Ensure that all options are ticked for audit-purposes.
¶ Advanced Auditing
We are almost there!
One final requirement is to ensure that we have visibility on events that may occur outside of the MMC snap-in.
Step 1.
Run the following commands (via an Administrator command prompt):
certutil –setreg CA\CRLPeriod Weeks
certutil –setreg CA\CRLPeriodUnits 2
Step 2.
Configure the Audit policy via the command line (local policy) or group policy.
Local policy via command line as follows:
auditpol /set /subcategory:"Registry" /success:enable /failure:enable
Via Group Policy
To set audit policy using group policies, configure the “Audit Registry” subcategory under Computer Configuration\Windows Settings\Security Settings\Advanced Audit Policy. Set the subcategory to be enabled for “success and failure”.
After enabling registry auditing, configure auditing for the Certification Services registry keys. To configure auditing for the AD CS CA registry key:
On each CA server…
- Open regedit, and navigate to HKLM\System\CurrentControlSet\Services\Certsvc\Configuration<YourCAName>
26/11/24 Edited HKLM\System\Services\CertSvc\Configuration\ changed to HKLM\System\CurrentControlSet\Services\Certsvc\Configuration<YourCAName>
-
Right-click the Configuration registry key and click Permissions…
-
Click Advanced.
-
Click Auditing.
-
Click Select a principal and select Authenticated Users. From the drop down menus, for Type select All and for Applies To, select This key and subkeys.
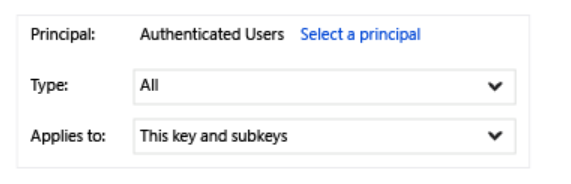
- Click Show advanced permissions and select the values shown below.
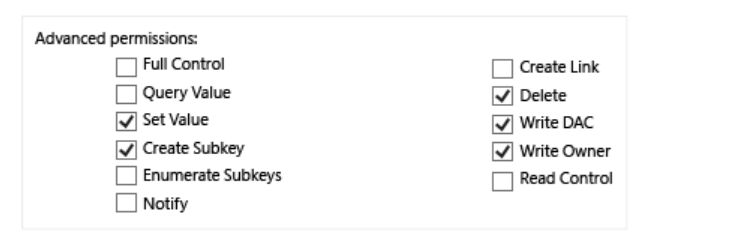
Once complete, please advise the SOC team, who will assist you in creating an event to test the auditing.
¶ Further reading
More information can be found on the follwing link(s):
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn786432(v=ws.11)
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn786422(v=ws.11)
¶ Certificate Services Events
| Event | Notes |
|---|---|
| 4868 | The certificate manager denied a pending certificate request. |
| 4869 | Certificate Services received a resubmitted certificate request. |
| 4870 | Certificate Services revoked a certificate. |
| 4871 | Certificate Services received a request to publish the certificate revocation list (CRL). |
| 4872 | Certificate Services published the certificate revocation list (CRL). |
| 4873 | A certificate request extension changed. |
| 4874 | One or more certificate request attributes changed. |
| 4875 | Certificate Services received a request to shut down. |
| 4876 | Certificate Services backup started. |
| 4877 | Certificate Services backup completed. |
| 4878 | Certificate Services restore started. |
| 4879 | Certificate Services restore completed. |
| 4880 | Certificate Services started. |
| 4881 | Certificate Services stopped. |
| 4882 | The security permissions for Certificate Services changed. |
| 4883 | Certificate Services retrieved an archived key. |
| 4884 | Certificate Services imported a certificate into its database. |
| 4885 | The audit filter for Certificate Services changed. |
| 4886 | Certificate Services received a certificate request. |
| 4887 | Certificate Services approved a certificate request and issued a certificate. |
| 4888 | Certificate Services denied a certificate request. |
| 4889 | Certificate Services set the status of a certificate request to pending. |
| 4890 | The certificate manager settings for Certificate Services changed. |
| 4891 | A configuration entry changed in Certificate Services. |
| 4892 | A property of Certificate Services changed. |
| 4893 | Certificate Services archived a key. |
| 4894 | Certificate Services imported and archived a key. |
| 4895 | Certificate Services published the CA certificate to Active Directory Domain Services. |
| 4896 | One or more rows have been deleted from the certificate database. |
| 4897 | Role separation enabled: |
| 4898 | Certificate Services loaded a template. |