¶ Active Directory Auditing
This page describes the steps to enable more granular Active Directory audit logs that can in turn be ingested and correlated in QRadar. This guide should be considered as minimum policy, and limited in scope to auditing changes made to Active Directory Users, Groups, Policies, and is not intended to prescribe final organisation wide audit policy.
The enhanced event visibility documented on this page provides more insight into a number of adversary techniques including:
> Reconnaissance
> Resource Development
> Persistence
> Privilege Escalation
> Defense Evasion
> Credential Access
> Lateral Movement
> Collection
Although the default Active Directory logging settings generate a range of events, the below settings will further enhance your logging capabilities and provide enriched data in the event of a security incident.
Some of the settings outlined may already be set as described within your environment, however it is advised that this be verified. Upon completion of the below steps, please inform the Secure-ISS SOC so that we can validate that the enhanced events are being received and correlated accordingly.
Note: The below steps are for Windows Server 2008 and above
The settings below will ensure appropriate minimum logging for events pertaining to and only to:
> Kerberos authentication ticket-granting ticket (TGT) requests.
> Computer accounts being created, changed, or deleted.
> Distribution-group management tasks.
> Security group management tasks.
> User account management tasks.
> Process being created / terminated.
> Changes made to objects in Active Directory Domain Services.
> Active Directory Domain Services objects being accessed.
> Events generated by RADIUS (IAS) and Network Access Protection (NAP) related to user access requests.
> Operations with scheduled tasks, COM+ objects and indirect object access requests.
> Changes made to authentication / authorisation policy.
> Startup, recovery, and shutdown events, and information about changes in system time.Wider audit policy should be considered and implemented as per Best Practice guidelines.
-
Open Group Policy Management Console
-
Right click / Edit “Default Domain Controllers Policy”
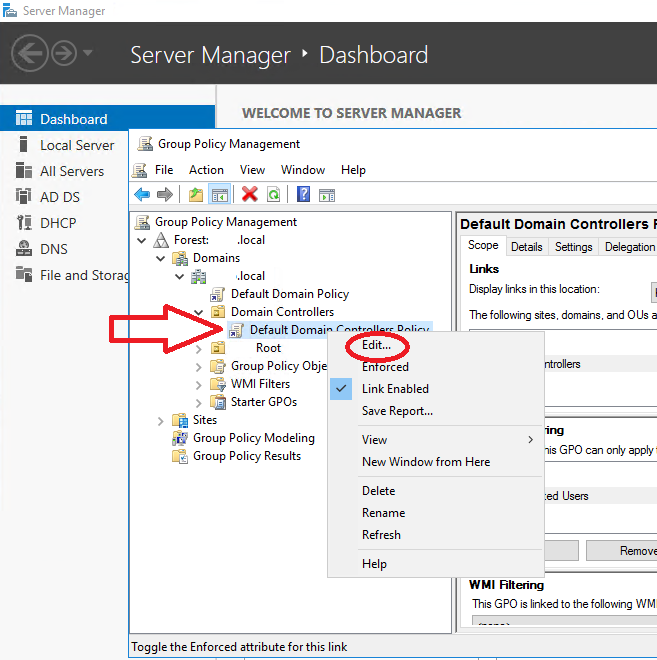
-
Configure as required
- Open Advanced Audit Policies
Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies
- Open Advanced Audit Policies
-
Audit policies
- Audit Logon Events: Select Account Logon
Audit ‘Kerberos Authentication Service’ (Success & Failure)
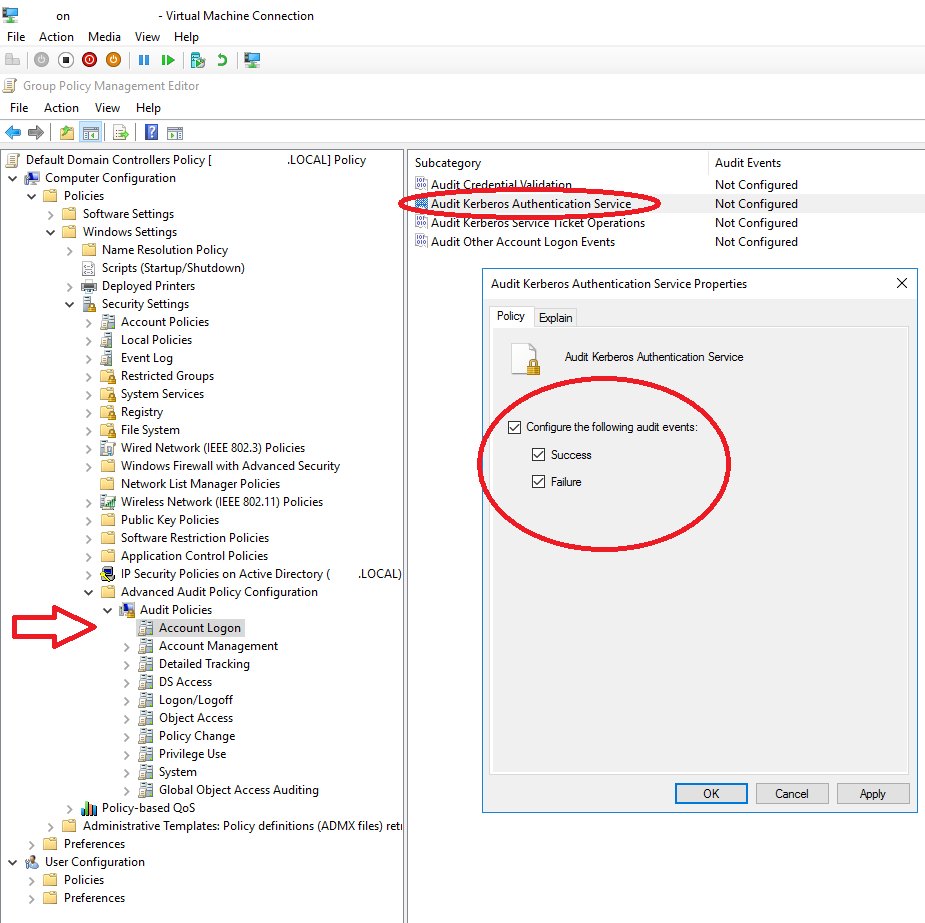
- Audit User, Group, Computer: Select Account Management
Audit ‘Computer Account Management’ (Success)
Audit ‘Distribution Group Management’ (Success)
Audit ‘Security Group Management’ (Success)
Audit ‘User Account Management’ (Success & Failure) - Audit tracking processes: Select Detailed Tracking
Audit Process Creation (Success)
Audit Process Termination (Success) - Audit GPO, OU, Configuration, Schema, Contacts, Containers, Sites, DNS: Select DS Access
Audit Directory Services Changes (Success) - Audit Logon / Logoff: Select Logon / Logoff
Audit Logon (Success & Failure)
Audit Logoff (Success)
Audit Network Policy Server (Success & Failure)
Audit Other Logon / Logoff Events (Success) - Audit Scheduled Tasks: Select Object Access
Audit Other Object Access Events (Success) - Audit Local Policy Changes: Select Policy Change
Audit Authentication Policy Change (Success)
Audit Authorization Policy Change (Success) - Audit System Events: Select System
Audit Security State Change (Success)
- Audit Logon Events: Select Account Logon
-
Computer Configuration > Policies > Windows Settings > Security Settings > Local Polices > Security Options
- Audit Force audit policy subcategory settings (Enabled)
¶ Configuring the System Access Control List
SACL’s are used to define security policies system wide. The settings below will ensure enhanced logging is in use, which will allow more thorough generation of events for auditing purposes. In addition to auditing, these logs are intended to enhance your security posture and assist in early detection of unusual or malicious activity.
Some of the settings outlined below may be in use within your organisation, it is advised that the following settings are verified.
To configure SACL, you must be either a member of the “Domain Admins” group, the Enterprise Admins group in Active Directory, or you must have been delegated the appropriate authority.
Any of the the below steps may skipped if they are not relevant for your organisation
¶ Steps to configure SACL- OU/GPO/Users/Groups/Computers/Contacts
- Open “Active Directory Users and Computers”
- Click “Start” -> “Control Panel” -> “Administrative Tools” -> “Active Directory Users and Computers”
- Ensure that “View” -> “Advanced Features” are selected from the drop down. This will display the Advanced Security settings for selected objects in the Active Directory Users and Computers.
- In the console tree, right-click the “Domain” root
- Click “Properties”, and then click the “Security” tab.
- Click “Advanced”
- Click on the “Auditing” Tab and Click “Add” to add new security principal you want to apply the security policy (In our case it is “Everyone”)
- Click on OK.
- This opens the window to select “Auditing Entry” for the Domain.
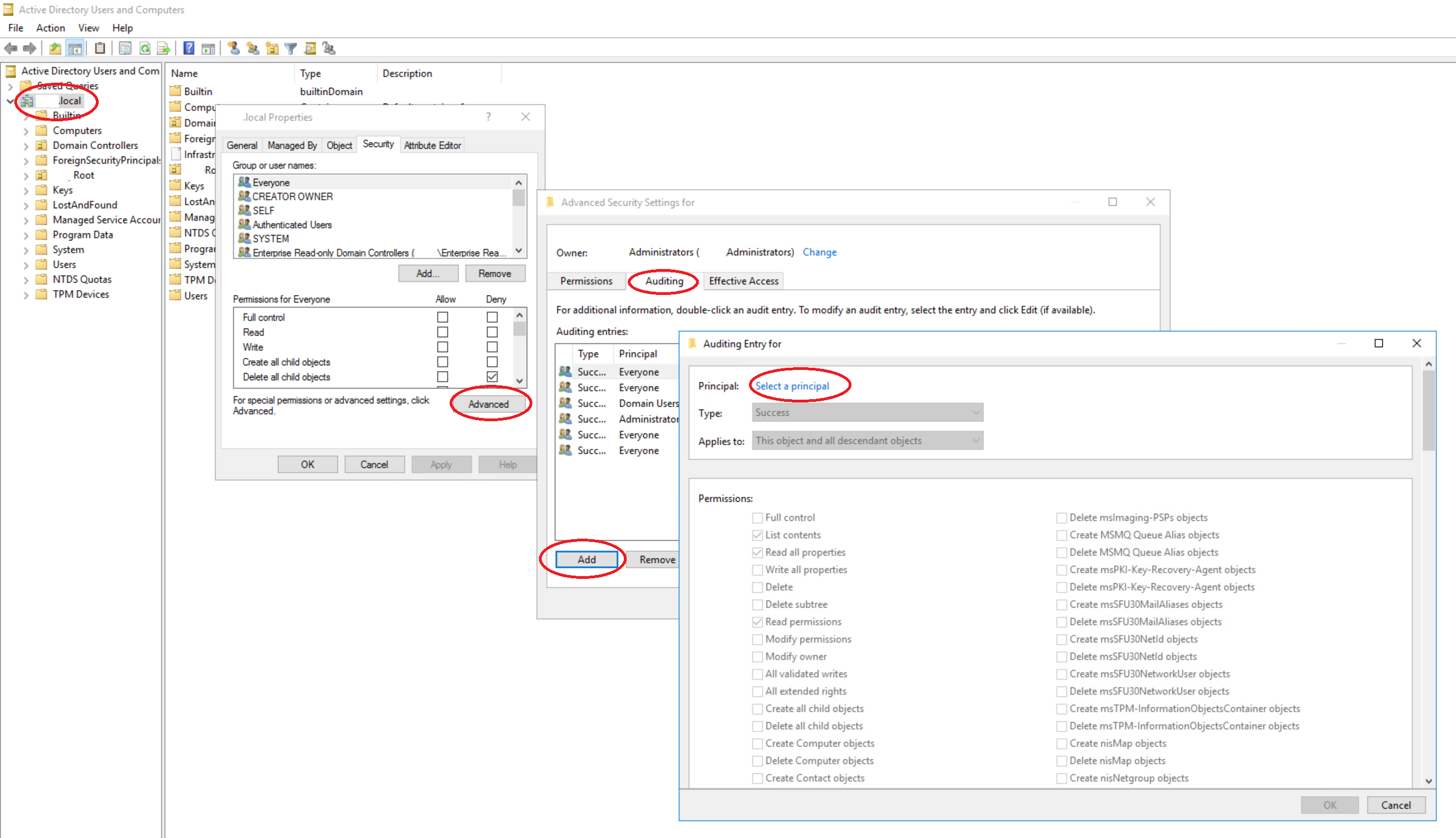
Configure the following where appropriate
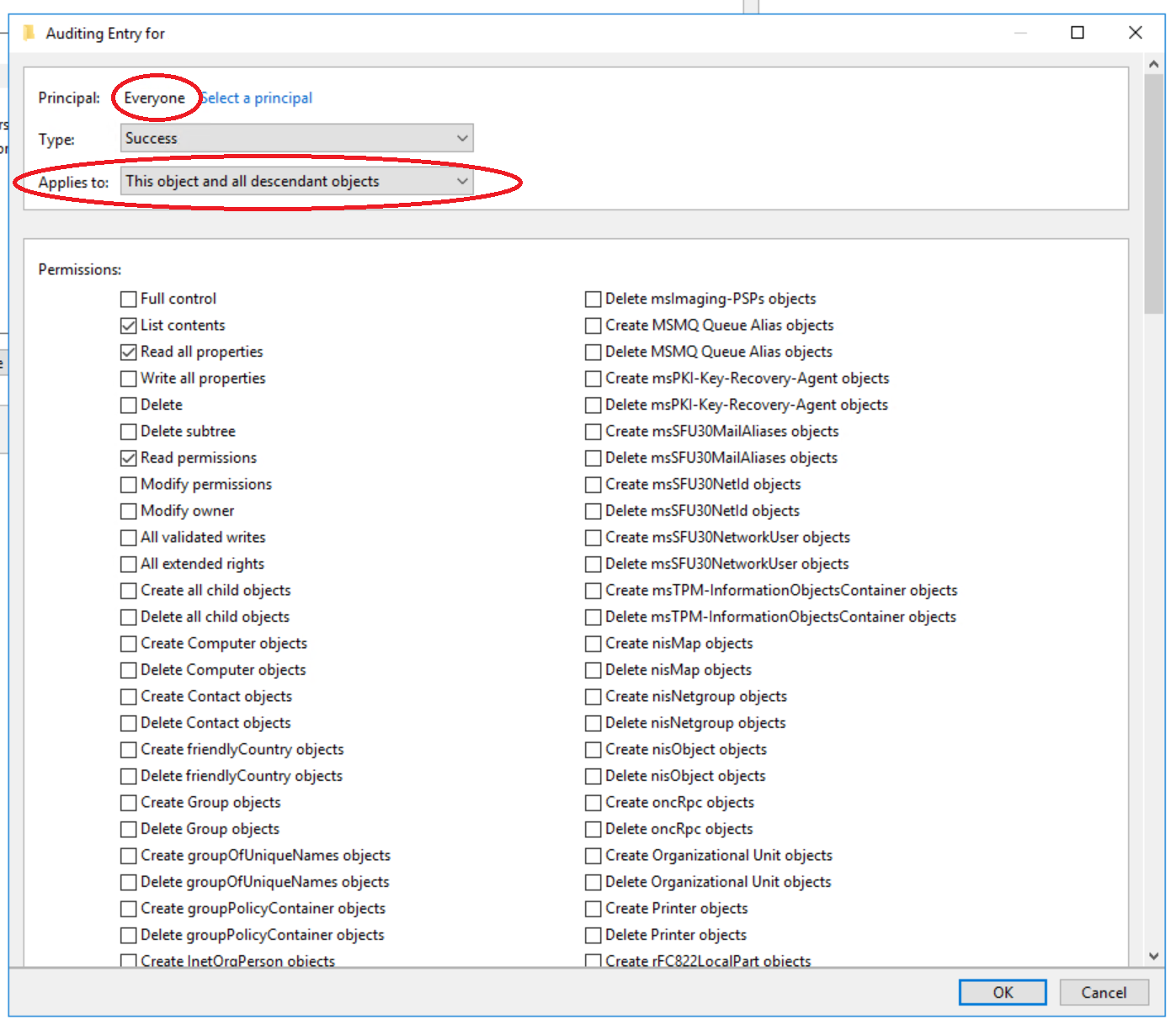
When you create the new ACL allowing access, some values will be selected automatically.
Ensure all checkboxes are cleared using the “Clear all” button if creating a new entry, this applies to all following entries. This button’s location requires you to scroll to the very bottom of list of permission flags.
Complete the above steps for all of the following
Ensure you are modifying the “Auditing” tab!
What is being defined here is whether or not an audit event should be generated for a given object, depending on who the user is and where the object is located. For example for the first listed below, we want to create an audit event when “Everyone”/Anyone creates an “Organisational Unit” in the root of the domain and all descendant objects
Eg: Set the “Applies To” field to This object and all descendant objects and check the following checkboxes. Then set the “Applies To” field to Descendant Organizational Unit objects and check the listed checkboxes and so on…
This object and all descendant objects
Permissions > Create Organizational Unit objects
Permissions > Delete Organizational Unit objects
Permissions > Create groupPolicyContainer Objects
Permissions > Delete groupPolicyContainer Objects
Descendant Organizational Unit objects
Permissions > Delete
Permissions > Modify Permissions
Properties > Write All Properties
Descendant groupPolicyContainer objects
Permissions > Delete
Permissions > Modify Permissions
Properties > Write All Properties
Descendant User objects
Permissions > Delete
Permissions > Modify Permissions
Permissions > All Extended Rights
Properties > Write All Properties
Descendant Group objects
Permissions > Delete
Permissions > Modify Permissions
Permissions > All Extended Rights
Properties > Write All Properties
Descendant Computer objects
Permissions > Delete
Permissions > Modify Permissions
Permissions > All Extended Rights
Properties > Write All Properties
Descendant Contact objects
Permissions > Delete
Permissions > Modify Permissions
Properties > Write All Properties
¶ Auditing entries for all Containers
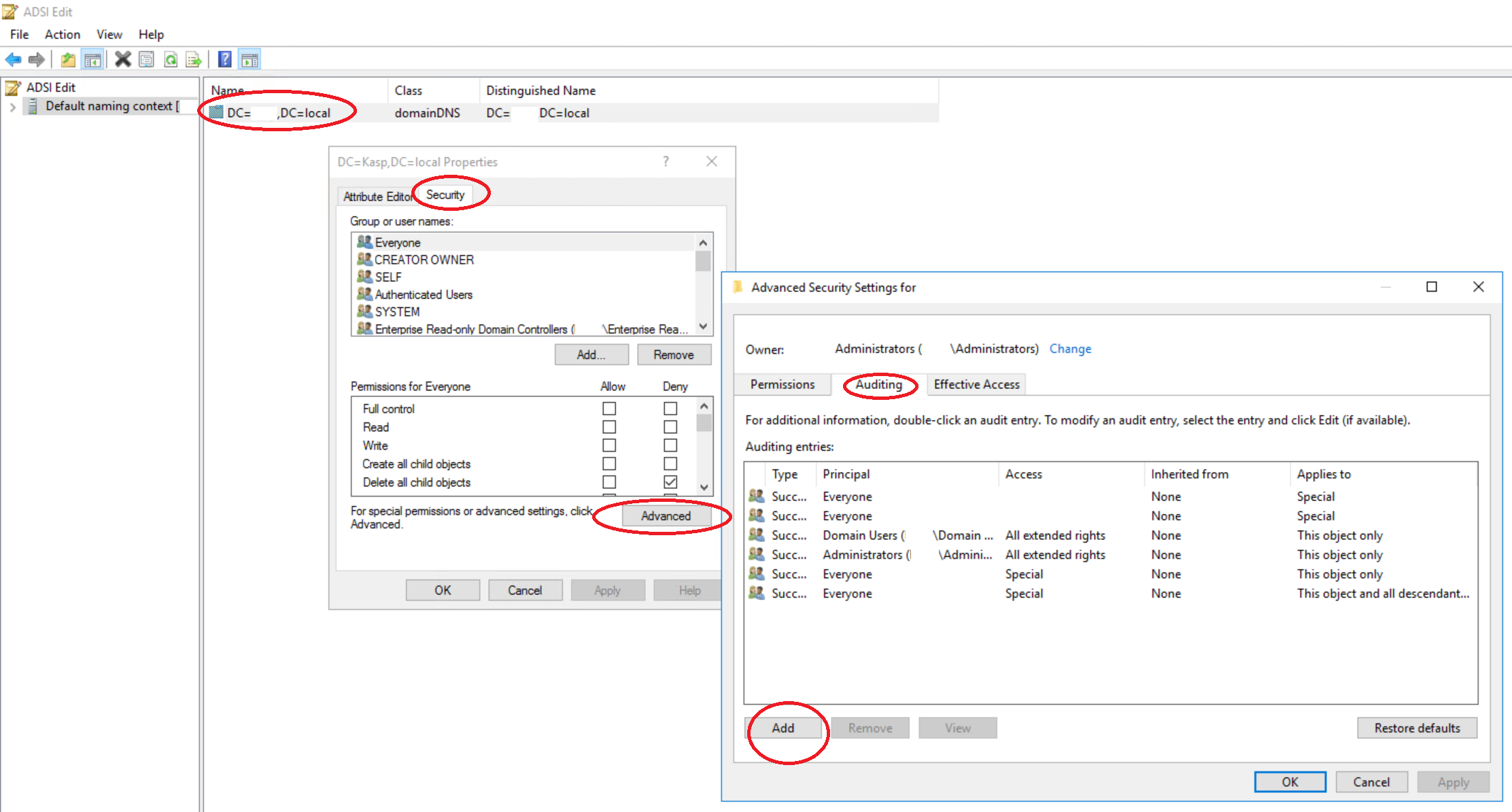
- Open Run Prompt (Windows+R) and type adsiedit.msc and press Enter.
- Right click on ADSI -> Edit -> Connect to…
- Under “Connection Point” -> Under “Select a Well Known Naming Context” -> Select “Default Naming Context” -> “OK”.
- Expand the Default naming context field.
- Right Click the ‘Domain’s distinguished name’ and Select “Properties” -> “Security”.
- Click on “Advanced” and select the “Auditing” Tab, click on “Add”
- Click on “Select principal” set the “Object name” to “Everyone”
- Set the properties to reflect the below list
¶ Containers
Descendant Container objects
Permissions > Delete
Permissions > Modify Permissions
Properties > Write All Properties
OK -> APPLY -> OK -> OK
¶ Auditing entries for all Password Setting objects
- Open Run Prompt (Windows+R) and type “adsiedit.msc” and press Enter.
- Right Click on “ADSI Edit” and select “Connect to…”
- Under “Connection Point” -> Under “Select a Well Known Naming Context” -> Select “Default Naming Context”.
- Click on “Default naming context”.
- Expand the Domain
- Expand the “System” container
- Right click on the “Password Settings Container” and click on “Properties”
- Go to “Security” tab and click on “Advanced”
- Select “Auditing” tab and click “Add”
- Click on “Select principal” set the “Object name” to “Everyone”
- Set the properties to reflect the below list
¶ Password Setting Container
Everyone - Success
This object and all descendant objects
Create msDS-PasswordSettings objects
Delete msDS-PasswordSetting objects
Descendant msDS-PasswordSettings objects
Write All Properties
Delete
Modify Permissions
OK -> APPLY -> OK -> OK
¶ Auditing entries for all Configuration/Schema
- Open Run Prompt (Windows+R) and type “adsiedit.msc” and press Enter.
- Right Click on “ADSI Edit” and select “Connect to…”
- Under “Connection Point” -> Under “Select a Well Known Naming Context” > Select “Configuration” / “Schema” (For Schema SACL).
- Double Click “Configuration” / “Schema” on the Left Pane.
- Right Click the Configuration Context / Schema Context and Select “Properties” > “Security”.
- Click on “Advanced” and Select the “Auditing” Tab.
- Follow the below steps.
Follow steps for either Configuration OR Schema, whichever is appropriate for your environment.
¶ Configuration / Schema
Everyone - Successful
This object and all descendant objects
Create All Child objects
Delete All child objects
Delete
Write All Properties
Modify Permissions
All Extended Rights
OK -> APPLY -> OK -> OK
¶ Auditing Entries for AD DNS objects
- Open Run Prompt (Windows+R) and type "adsiedit.msc" and press Enter.
- Right Click on "ADSI Edit" and select "Connect to.."
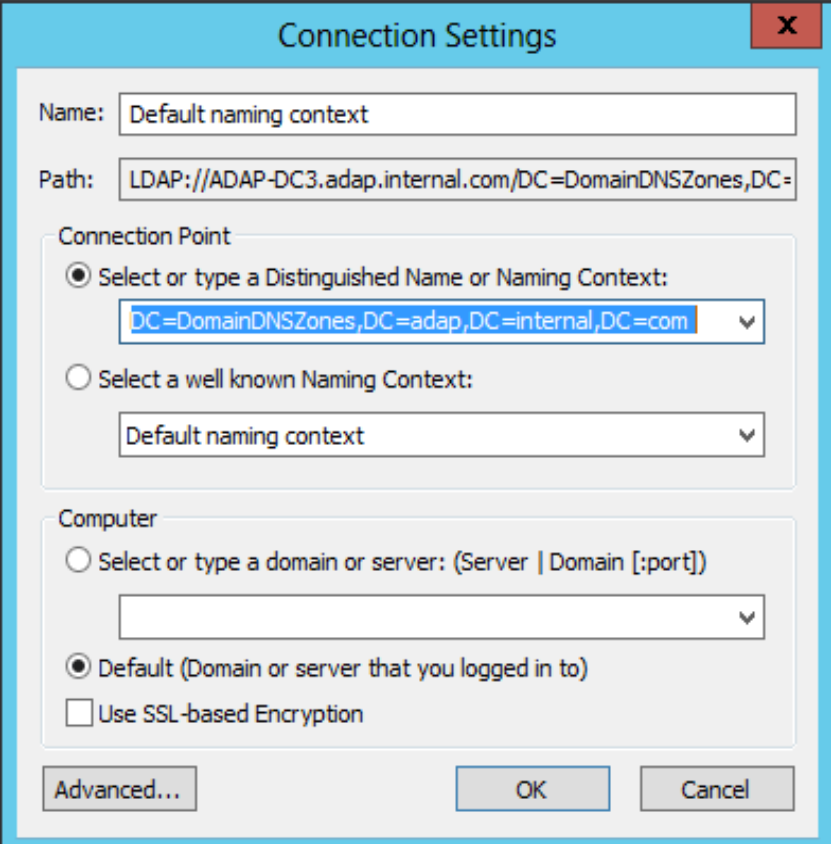
- Under "Connection Point" -> Under Select or type a Distinguished Name or Naming Context:
- Substitute XXXXX as appropriate
- Type "DC=XXXXX, DC=XXXXX,DC=XXXXX" as the Distinguished Name. (This partition is generally loaded in Adsiedit by default)
- Type "DC=DomainDNSZones, DC=XXXXX, DC=XXXXX, DC=XXXXX" as the Distinguished Name.
- Type "DC=ForestDNSZones, DC=XXXXX, DC=XXXXX, DC=XXXXX" as the Distinguished Name.
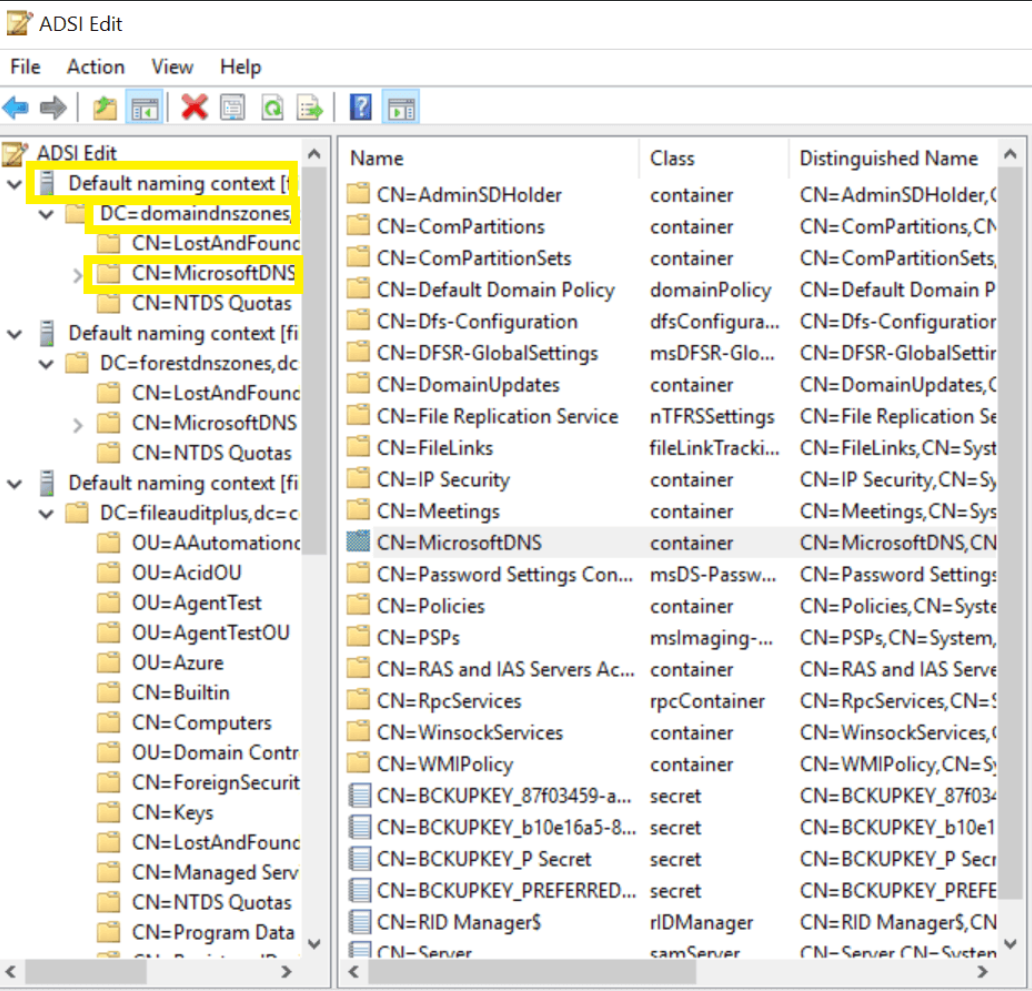
- Double Click "Default Naming Context" on the Left Pane.
- Right Click the "MicrosoftDNS Container" and Select "Properties" > "Security"
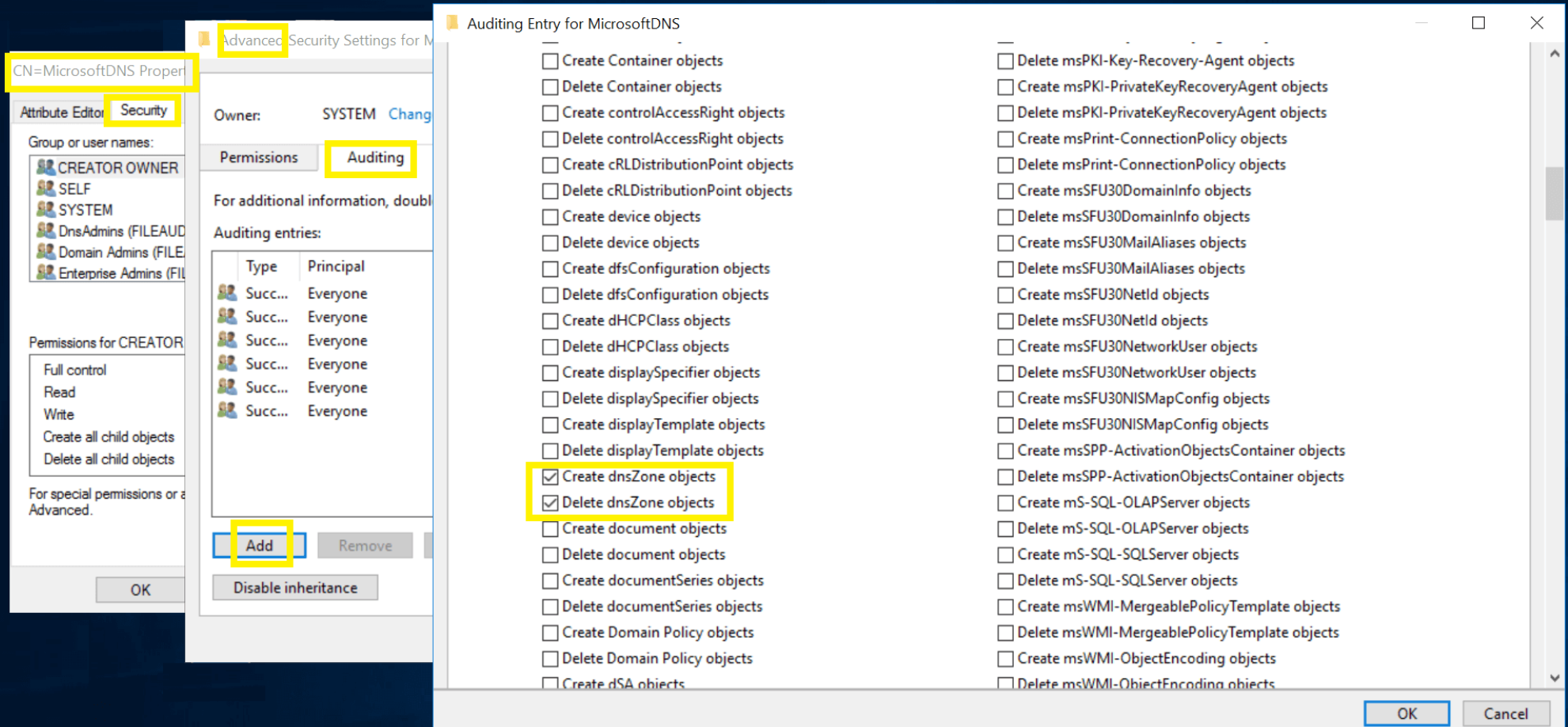
- Click on "Advanced" and Select the "Auditing" Tab, click Add
- In the "Auditing Entry" window > Select a principal > "Everyone" > "OK"
- Set "Type" to Success
- Select the appropriate permissions, as directed below.
¶ DNS Zones
Create DNS Zones objects - This object and all descendant objects
Delete DNS Zones objects - This object and all descendant objects
Write All Properties - Descendant DNS Zone objects
Delete - Descendant DNS Zone objects
Modify Permissions - Descendant DNS Zone objects
¶ DNS Nodes
Create DNS Nodes objects - Descendant DNS Zone objects
Delete DNS Nodes objects - Descendant DNS Zone objects
Write All Properties - Descendant DNS Node objects
Delete - Descendant DNS Node objects
Modify Permissions - Descendant DNS Node objects
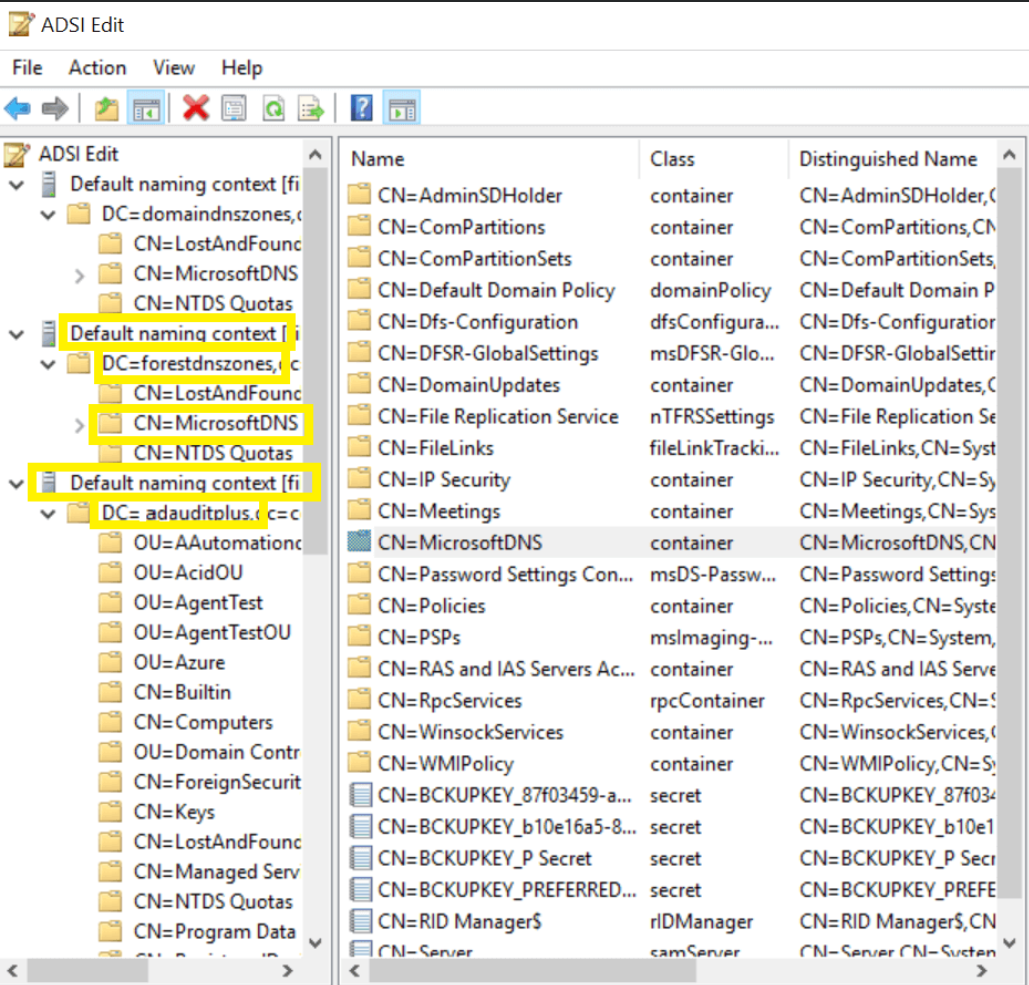
¶ Repeat steps 4 - 9 for the remaining 2 default naming contexts