¶ Palo Alto Log Forwarding Setup Guide
¶ Take care
Palo Alto logs are some of the most detailed logs available to be ingested from a firewall, however there is a fair bit of configuration work required and it is easy to make mistakes/oversights. We urge you to both read and execute these instructions with great care and recommend against rushing through.
These includes configuring custom syslog output formats.
Configuring forwarding on per-rule basis
Configuring some global forwarding, for example System, Configuration and GlobalProtect/Auth logging.
¶ These instructions will and have changed over time
If you have been directed here after your initial setup, please follow through this guide again, ensuring your current configuration matches, as this setup process has evolved over time and with later releases of PanOS and revisions to the QRadar Palto Alto Integrations.
This mostly applies to the Syslog Server Profile / Log Type configuration, where the Syslog Format Template has been changed, particlarly after the PanOS 11.0 release, as well as the 10.1/10.2 releases. These releases added new features, and enrichments to existing event types, which requires the format to be updated to be included.
We recommend you run through the Syslog Server Profile setup again in it’s entirity, copy pasting each profile again, and nearly every template has been changed at some point.
¶ Intro
Please follow the instructions below to forward log events from your Palo Alto Networks Firewall to the QRadar SIEM.
- Navigate to the Device tab, open Server Profiles > Syslog
- Configure the address of the QRadar Processor or Collector that the firewall should send events to as per screenshot below.
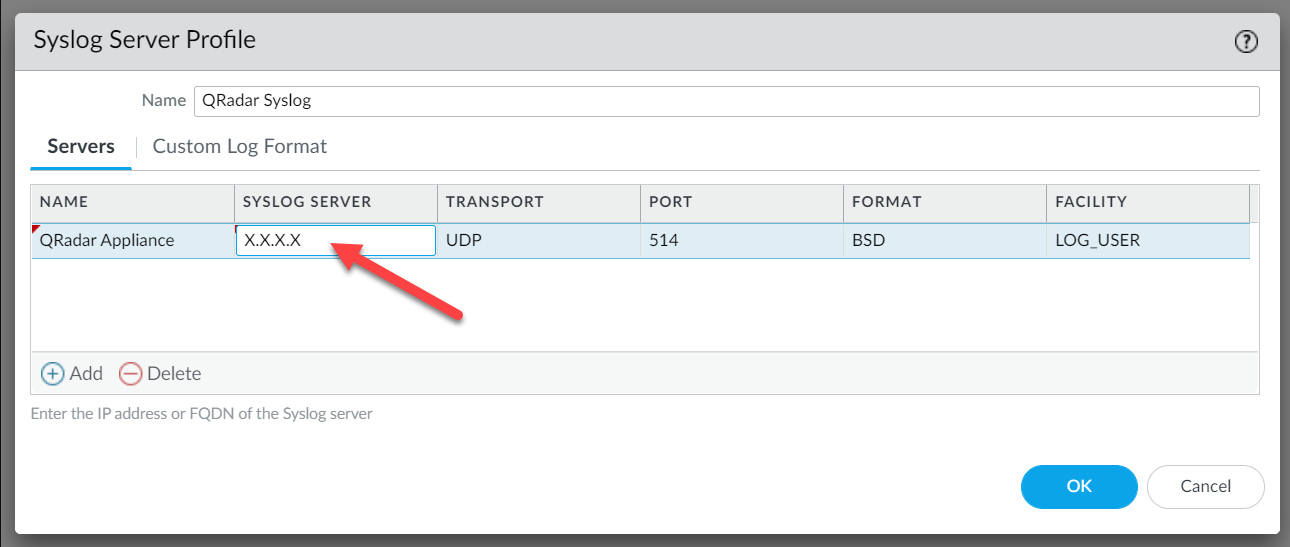
¶ Preparing to Forward Logs
¶ Syslog Profile
On the Custom Log Format tab of the Syslog Server Profile, the custom formats must be entered for each of the log types.
Copy each of the Log Type Entries (below) and paste into the corresponding field.
The screenshot below displays how these would look.
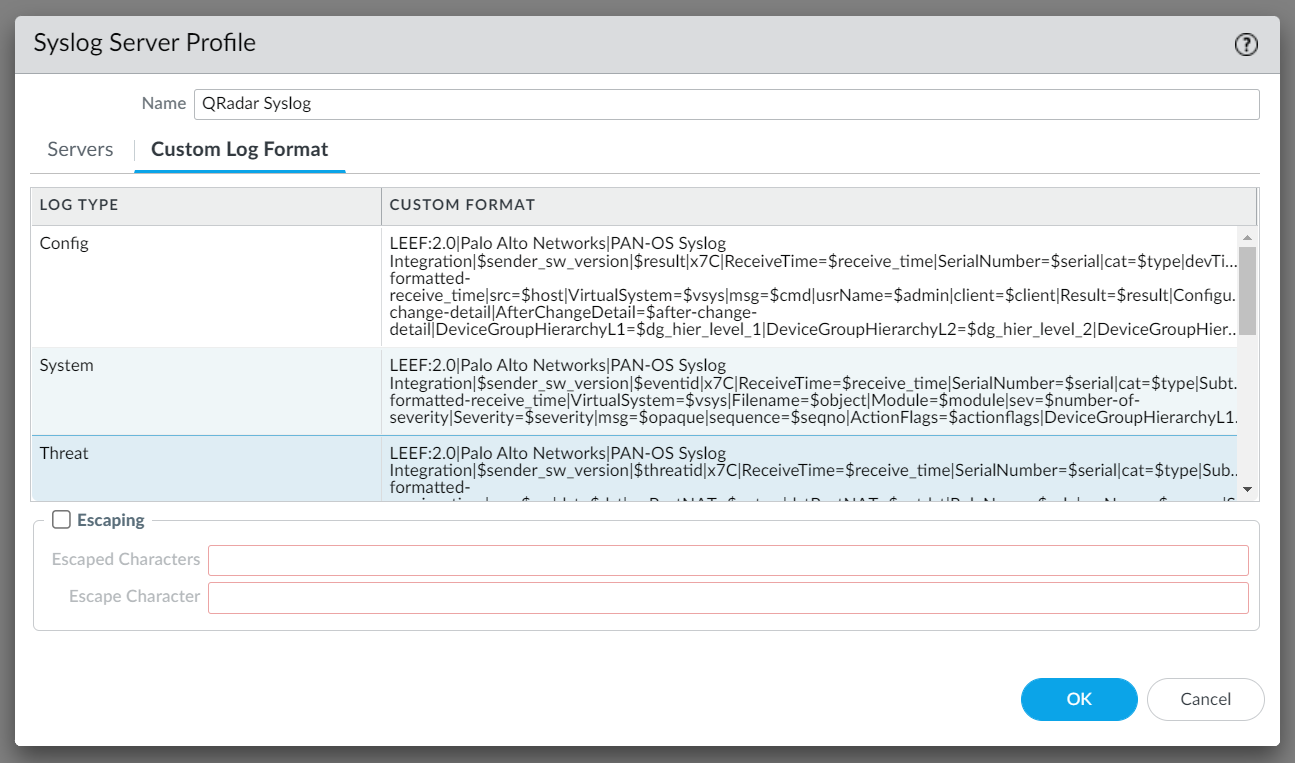
NOTE: This is of critical importance or QRadar will not be able to interpret the log data
¶ Config
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$result|x7C|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|devTime=$cef-formatted-receive_time|src=$host|VirtualSystem=$vsys|msg=$cmd|usrName=$admin|client=$client|Result=$result|ConfigurationPath=$path|sequence=$seqno|ActionFlags=$actionflags|BeforeChangeDetail=$before-change-detail|AfterChangeDetail=$after-change-detail|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|DeviceGroupHierarchyL4=$dg_hier_level_4|vSrcName=$vsys_name|DeviceName=$device_name
¶ System
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$eventid|x7C|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|Subtype=$subtype|devTime=$cef-formatted-receive_time|VirtualSystem=$vsys|Filename=$object|Module=$module|sev=$number-of-severity|Severity=$severity|msg=$opaque|sequence=$seqno|ActionFlags=$actionflags|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|DeviceGroupHierarchyL4=$dg_hier_level_4|vSrcName=$vsys_name|DeviceName=$device_name
¶ Threat
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$threatid|x7C|ReceiveTime=$receive_time|SerialNumber=$serial|cat=$type|Subtype=$subtype|devTime=$cef-formatted-receive_time|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|RuleName=$rule|usrName=$srcuser|SourceUser=$srcuser|DestinationUser=$dstuser|Application=$app|VirtualSystem=$vsys|SourceZone=$from|DestinationZone=$to|IngressInterface=$inbound_if|EgressInterface=$outbound_if|LogForwardingProfile=$logset|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$sport|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|Flags=$flags|proto=$proto|action=$action|Miscellaneous=$misc|ThreatID=$threatid|URLCategory=$category|sev=$number-of-severity|Severity=$severity|Direction=$direction|sequence=$seqno|ActionFlags=$actionflags|SourceLocation=$srcloc|DestinationLocation=$dstloc|ContentType=$contenttype|PCAP_ID=$pcap_id|FileDigest=$filedigest|Cloud=$cloud|URLIndex=$url_idx|RequestMethod=$http_method|Subject=$subject|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|DeviceGroupHierarchyL4=$dg_hier_level_4|vSrcName=$vsys_name|DeviceName=$device_name|SrcUUID=$src_uuid|DstUUID=$dst_uuid|TunnelID=$tunnelid|MonitorTag=$monitortag|ParentSessionID=$parent_session_id|ParentStartTime=$parent_start_time|TunnelType=$tunnel|ThreatCategory=$thr_category|ContentVer=$contentver
¶ Traffic
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$action|x7C|cat=$type|devTime=$cef-formatted-receive_time|SerialNumber=$serial|Subtype=$subtype|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|RuleName=$rule|usrName=$srcuser|DestinationUser=$dstuser|Application=$app|VirtualSystem=$vsys|SourceZone=$from|DestinationZone=$to|IngressInterface=$inbound_if|EgressInterface=$outbound_if|LogForwardingProfile=$logset|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$sport|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|Flags=$flags|proto=$proto|totalBytes=$bytes|srcBytes=$bytes_sent|dstBytes=$bytes_received|totalPackets=$packets|dstPackets=$pkts_received|srcPackets=$pkts_sent|start=$cef-formatted-time_generated|ElapsedTime=$elapsed|URLCategory=$category|sequence=$seqno|SessionEndReason=$session_end_reason|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|vSrcName=$vsys_name|DeviceName=$device_name|ActionSource=$action_source|ActionFlags=$actionflags|SrcUUID=$src_uuid|DstUUID=$dst_uuid|TunnelID=$tunnelid|MonitorTag=$monitortag|ParentSessionID=$parent_session_id|ParentStartTime=$parent_start_time|TunnelType=$tunnelRuleUUID=$rule_uuid|PolicyID=$policy_id|LinkDetail=$link_switches|SDWANCluster=$sdwan_cluster|SDWANDevice=$sdwan_device_type|SDWANClustype=$sdwan_cluster_type|SDWANSite=$sdwan_site|DynamicUsrgrp=$dynusergroup_name|XFFIP=$xff_ip|SrcDeviceCat=$src_category|SrcDeviceProf=$src_profile|SrcDeviceModel=$src_model|SrcDeviceVendor=$src_vendor|SrcDeviceOS=$src_osfamily|SrcDeviceOSv=$src_osversion|SrcHostname=$src_host|SrcMac=$src_mac|DstDeviceCat=$dst_category|DstDeviceProf=$dst_profile|DstDeviceModel=$dst_model|DstDeviceVendor=$dst_vendor|DstDeviceOS=$dst_osfamily|DstDeviceOSv=$dst_osversion|DstHostname=$dst_host|DstMac=$dst_mac|ContainerName=$container_id|PODNamespace=$pod_namespace|PODName=$pod_name|SrcEDL=$src_edl|DstEDL=$dst_edl|GPHostID=$hostid|EPSerial=$serialnumber|SrcDAG=$src_dag|DstDAG=$dst_dag
¶ URL
LEEF:2.0|Palo Alto Networks|Next Generation Firewall|$sender_sw_version|$threatid|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|Rule=$rule|usrName=$srcuser|DestinationUser=$dstuser|Application=$app|VirtualLocation=$vsys|FromZone=$from|ToZone=$to|InboundInterface=$inbound_if|OutboundInterface=$outbound_if|LogSetting=$logset|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$sport|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|proto=$proto|Action=$action|URL=$file_url|VendorSeverity=$severity|DirectionOfAttack=$direction|SequenceNo=$seqno|SourceLocation=$srcloc|DestinationLocation=$dstloc|ContentType=$contenttype|PacketID=$pcap_id|URLCounter=$url_idx|UserAgent=$user_agent|identSrc=$xff|Referer=$referer|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|SourceUUID=$src_uuid|DestinationUUID=$dst_uuid|HTTPMethod=$http_method|IMSI=$imsi|IMEI=$imei|ParentSessionID=$parent_session_id|ParentStarttime=$parent_start_time|Tunnel=$tunnelid|InlineMLVerdict=unknown|ContentVersion=$contentver|SigFlags=$sig_flags|HTTPHeaders=$http_headers|URLCategoryList=$url_category_list|RuleUUID=$rule_uuid|HTTP2Connection=$http2_connection|DynamicUserGroupName=$dynusergroup_name|X-Forwarded-ForIP=$xff_ip|SourceDeviceCategory=$src_category|SourceDeviceProfile=$src_profile|SourceDeviceModel=$src_model|SourceDeviceVendor=$src_vendor|SourceDeviceOSFamily=$src_osfamily|SourceDeviceOSVersion=$src_osversion|SourceDeviceHost=$src_host|SourceDeviceMac=$src_mac|DestinationDeviceCategory=$dst_category|DestinationDeviceProfile=$dst_profile|DestinationDeviceModel=$dst_model|DestinationDeviceVendor=$dst_vendor|DestinationDeviceOSFamily=$dst_osfamily|DestinationDeviceOSVersion=$dst_osversion|DestinationDeviceHost=$dst_host|DestinationDeviceMac=$dst_mac|ContainerID=$container_id|ContainerNameSpace=$pod_namespace|ContainerName=$pod_name|SourceEDL=$src_edl|DestinationEDL=$dst_edl|HostID=$hostid|EndpointSerialNumber=$serialnumber|SourceDynamicAddressGroup=$src_dag|DestinationDynamicAddressGroup=$dst_dag|TimeGeneratedHighResolution=$high_res_timestamp|NSSAINetworkSliceType=$nssai_sst|devTimeFormat=$cef-formatted-time_generated
¶ Data
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$threatid|x7C|ReceiveTime=$receive_time|SerialNumber=$serial|cat=$type|Subtype=$subtype|devTime=$cef-formatted-receive_time|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|RuleName=$rule|usrName=$srcuser|SourceUser=$srcuser|DestinationUser=$dstuser|Application=$app|VirtualSystem=$vsys|SourceZone=$from|DestinationZone=$to|IngressInterface=$inbound_if|EgressInterface=$outbound_if|LogForwardingProfile=$logset|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$sport|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|Flags=$flags|proto=$proto|action=$action|Miscellaneous=$misc|ThreatID=$threatid|URLCategory=$category|sev=$number-of-severity|Severity=$severity|Direction=$direction|sequence=$seqno|ActionFlags=$actionflags|SourceLocation=$srcloc|DestinationLocation=$dstloc|ContentType=$contenttype|PCAP_ID=$pcap_id|FileDigest=$filedigest|Cloud=$cloud|URLIndex=$url_idx|RequestMethod=$http_method|Subject=$subject|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|DeviceGroupHierarchyL4=$dg_hier_level_4|vSrcName=$vsys_name|DeviceName=$device_name|SrcUUID=$src_uuid|DstUUID=$dst_uuid|TunnelID=$tunnelid|MonitorTag=$monitortag|ParentSessionID=$parent_session_id|ParentStartTime=$parent_start_time|TunnelType=$tunnel|ThreatCategory=$thr_category|ContentVer=$contentver
¶ Wildfire
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$threatid|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|Rule=$rule|usrName=$srcuser|DestinationUser=$dstuser|Application=$app|VirtualLocation=$vsys|FromZone=$from|ToZone=$to|InboundInterface=$inbound_if|OutboundInterface=$outbound_if|LogSetting=$logset|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$spor|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|proto=$proto|Action=$action|FileName=$misc|URLCategory=$category|VendorSeverity=$severity|DirectionOfAttack=$direction|SequenceNo=$seqno|SourceLocation=$srcloc|DestinationLocation=$dstloc|PacketID=$pcap_id|FileHash=$filedigest|ApplianceOrCloud=$cloud
¶ Tunnel
LEEF:2.0|Palo Alto Networks|Next Generation Firewall|$sender_sw_version|$action|x7C|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|Rule=$rule|usrName=$srcuser|DestinationUser=$dstuse|Application=$app|VirtualLocation=$vsys|FromZone=$from|ToZone=$to|InboundInterface=$inbound_if|OutboundInterface=$outbound_if|LogSetting=$logset|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$sport|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|proto=$proto|SequenceNo=$seqno|SourceLocation=$srcloc|DestinationLocation=$dstloc|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|ParentSessionID=$parent_session_id|ParentStarttime=$parent_start_time|Tunnel=$tunnel|Bytes=$bytes|srcBytes=$bytes_sent|dstBytes=$bytes_received|totalPackets=$packets|srcPackets=$pkts_sent|dstPackets=$pkts_received|TunnelSessionsCreated=$sessions_created|TunnelSessionsClosed=$sessions_closed|SessionEndReason=$session_end_reason|ActionSource=$action_source|startTime=$start|SessionDuration=$elapsed|RuleUUID=$rule_uuid|DynamicUserGroupName=$dynusergroup_name|ContainerID=$container_id|ContainerNameSpace=$pod_namespace|ContainerName=$pod_name|SourceEDL=$src_edl|DestinationEDL=$dst_edl|SourceDynamicAddressGroup=$src_dag|DestinationDynamicAddressGroup=$dst_dag|TimeGeneratedHighResolution=$high_res_timestamp|NSSAINetworkSliceDifferentiator=$nssai_sd|NSSAINetworkSliceType=$nssai_sst|ProtocolDataUnitsessionID=$pdu_session_id|devTimeFormat=$cef-formatted-time_generated
¶ Authentication
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$event|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|VirtualLocation=$vsys|src=$ip|User=$normalize_user|usrName=$user|Object=$object|object2AuthenticationPolicy=$authpolicy|CountOfRepeats=$repeatcnt|MFAAuthenticationID=$authid|MFAVendor=$vendor|LogSetting=$logset|AuthServerProfile=$serverprofile|AuthenticationDescription=$desc|ClientType=$clienttype|AuthFactorNo=$factorno|SequenceNo=$seqno|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|VirtualSystemID=$vsys_id|AuthenticationProtocol=$authproto|RuleMatchedUUID=$rule_uuid|TimeGeneratedHighResolution=$high_res_timestamp|SourceDeviceCategory=$src_category|SourceDeviceProfile=$src_profile|SourceDeviceModel=$src_model|SourceDeviceVendor=$src_vendor|SourceDeviceOSFamily=$src_osfamily|SourceDeviceOSVersion=$src_osversion|SourceDeviceHost=$src_host|SourceDeviceMac=$src_mac|AuthCacheServiceRegion=$region|UserAgentString=$user_agent|SessionID=$sessionid|devTimeFormat=$cef-formatted-time_generated
¶ User-ID
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$subtype|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|VirtualLocation=$vsys|src=$ip|usrName=$user|MappingDataSourceName=$datasourcename|EventIdName=$eventid|CountofRepeats=$repeatcnt|MappingTimeout=$timeout|srcPort=$beginport|dstPort=$endport|MappingDataSource=$datasource|MappingDataSourceType=$datasourcetype|SequenceNo=$seqno|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|VirtualSystemID=$vsys_id|MFAFactorType=$factortype|AuthCompletionTime=$factorcompletiontime|AuthFactorNo=$factorno|UGFlags=$ugflags|UserIdentifiedBySource=$userbysource|Tag=$tag_name|TimeGeneratedHighResolution=$high_res_timestamp|devTimeFormat=$cef-formatted-time_generated
¶ HIP Match
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$matchname|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|usrName=$srcuser|VirtualLocation=$vsys|identHostName=$machinename|EndpointOSType=$os|iOSsrc=$src|CountOfRepeats=$repeatcnt|SequenceNo=$seqno|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|VirtualSystemID=$vsys_id|SourceIPv6=$srcipv6|HostID=$hostid|EndpointSerialNumber=$serialnumber|SourceDeviceCategory=$reclassified|SourceDeviceModel=$matchtype|SourceDeviceMac=$mac|TimestampDeviceIdentification=$time_generated|TimeGeneratedHighResolution=$high_res_timestamp|devTimeFormat=$cef-formatted-time_generated
¶ GlobalProtect
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$eventid|x7C|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|VirtualSystem=$vsys|Stage=$stage|AuthMethod=$auth_method|TunnelType=$tunnel_type|usrName=$srcuser|SourceRegion=$srcregion|EndpointDeviceName=$machinename|PublicIPv4=$public_ip|PublicIPv6=$public_ipv6|PrivateIPv4=$private_ip|PrivateIPv6=$private_ipv6|HostID=$hostid|EndpointSN=$serialnumber|GlobalProtectClientVersion=$client_ver|EndpointOSType=$client_os|EndpointOSVersion=$client_os_ver|CountOfRepeats=$repeatcnt|QuarantineReason=$reason|ConnectionError=$error|Description=$opaque|EventStatus=$status|GlobalProtectGatewayLocation=$location|LoginDuration=$login_duration|ConnectionMethod=$connect_method|ConnectionErrorID=$error_code|Portal=$portal|SequenceNo=$seqno|TimeGeneratedHighResolution=$high_res_timestamp|GatewaySelectionType=$selection_type|SSLResponseTime=$response_time|GatewayPriority=$priority|AttemptedGateways=$attempted_gateways|Gateway=$gateway|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|VirtualSystemID=$vsys_id|devTimeFormat=$cef-formatted-time_generated
¶ IPtag
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$event_id|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat=$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|VirtualLocation=$vsys|src=$ip|TagName=$tag_name|CountOfRepeats=$repeatcnt|MappingTimeout=$timeout|MappingDataSource=$datasourcename|MappingDataSourceType=$datasource_type|MappingDataSourceSubType=$datasource_subtype|SequenceNo=$seqno|DGHierarchyLevel1=$dg_hier_level_1|DGHierarchyLevel2=$dg_hier_level_2|DGHierarchyLevel3=$dg_hier_level_3|DGHierarchyLevel4=$dg_hier_level_4|VirtualSystemName=$vsys_name|DeviceName=$device_name|VirtualSystemID=$vsys_id|IPSubnetRange=$ip_subnet_range|TimeGeneratedHighResolution=$high_res_timestamp|devTimeFormat=$cef-formatted-time_generated
¶ DNS (If applicable, 11.0.4+)
LEEF:2.0|Palo Alto Networks|Prisma Access|$sender_sw_version|$verdict|x7C|ProfileToken=$actionflags|DeviceSN=$log_source_id|TimeReceived=$time_generated|cat=$log_type|DNSResponseCode=$dns_response_code|UsrName=$source_user|LogSource=$log_source|url=$fqdn|SubType=$subtype|devTime=$time_generated|RecordType=$record_type|DNSResolverIP=$dest_ip|ThreatID=$gtid|ThreatName=$threat_name|src=$source_ip|FromZone=$from_zone|Action=$action|DNSResponse=$dns_response|ToZone=$dst_zone|DestinationUser=$dst_user
¶ (If applicable, <=9.1) Correlation
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|8.0|$category|x7C|ReceiveTime=$receive_time|SerialNumber=$serial|cat=$type|devTime=$cef-formatted-receive_time|startTime=$cef-formatted-time_generated|Severity=$severity|VirtualSystem=$vsys|VirtualSystemID=$vsys_id|src=$src|SourceUser=$srcuser|msg=$evidence|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|DeviceGroupHierarchyL4=$dg_hier_level_4|vSrcName=$vsys_name|DeviceName=$device_name|ObjectName=$object_name|ObjectID=$object_id
¶ (If applicable, <=9.1) SCTP
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$action|x7C|ReceiveTime=$receive_time|SerialNumber=$serial|cat=$type|genTime=$time_generated|src=$src|dst=$dst|VirtualSystem=$vsys|SourceZone=$from|DestinationZone=$to|IngressInterface=$inbound_if|EgressInterface=$outbound_if|SessionID=$sessionid|RepeatCount=$repeatcnt|srcPort=$sport|dstPort=$dport|proto=$proto|action=$action|DeviceGroupHierarchyL1=$dg_hier_level_1|DeviceGroupHierarchyL2=$dg_hier_level_2|DeviceGroupHierarchyL3=$dg_hier_level_3|DeviceGroupHierarchyL4=$dg_hier_level_4|vsysName=$vsys_name|DeviceName=$device_name|sequence=$seqno|AssocID=$assoc_id|PayloadProtoID=$ppid|sev=$num_of_severity|SCTPChunkType=$sctp_chunk_type|SCTPVerTag1=$verif_tag_1|SCTPVerTag2=$verif_tag_2|SCTPCauseCode=$sctp_cause_code|DiamAppID=$diam_app_id|DiamCmdCode=$diam_cmd_code|DiamAVPCode=$diam_avp_code|SCTPStreamID=$stream_id|SCTPAssEndReason=$assoc_end_reason|OpCode=$op_code|CPSSN=$sccp_calling_ssn|CPGlobalTitle=$sccp_calling_gt|SCTPFilter=$sctp_filter|SCTPChunks=$chunks|SrcSCTPChunks=$chunks_sent|DstSCTPChunks=$chunks_received|Packets=$packets|srcPackets=$pkts_sent|dstPackets=$pkts_received
¶ Decryption
LEEF:2.0|Palo Alto Networks|PAN-OS Syslog Integration|$sender_sw_version|$proxy_type|x7C|ProfileToken=$actionflags|TimeReceived=$receive_time|DeviceSN=$serial|cat$type|SubType=$subtype|ConfigVersion=$sender_sw_version|devTime=$cef-formatted-receive_time|src=$src|dst=$dst|srcPostNAT=$natsrc|dstPostNAT=$natdst|Rule=$rule|usrName=$srcuser|DestinationUser=$dstuser|Application=$app|VirtualLocation=$vsys|FromZone=$from|ToZone=$to|InboundInterface=$inbound_if|OutboundInterface=$outbound_if|LogSetting=$logset|TimeReceivedManagementPlane=$time_received|SessionID=$sessionid|CountOfRepeat=$repeatcnt|srcPort=$sport|dstPort=$dport|srcPostNATPort=$natsport|dstPostNATPort=$natdport|proto=$proto|Action=$action|Tunnel=$tunnel|SourceUUID=$src_uuid|DestinationUUID=$dst_uuid|RuleUUID=$rule_uuid|TLSVersion=$tls_version|TLSKeyExchange=$tls_keyxchg|TLSEncryptionAlgorithm=$tls_enc|TLSAuth=$tls_auth|PolicyName=$policy_name|EllipticCurve=$ec_curve|ErrorIndex=$err_index|RootStatus=$root_status|ChainStatus=$chain_status|CertificateSerial=$cert_serial|Fingerprint=$fingerprint|TimeNotBefore=$notbefore|TimeNotAfter=$notafter|CertificateVersion=$cert_ver|CertificateSize=$cert_size|CommonNameLength=$cn_len|IssuerNameLength=$issuer_len|RootCNLength=$rootcn_len|SNILength=$sni_len|CertificateFlags=$cert_flags|CommonName=$cn|IssuerCommonName=$issuer_cn|RootCommonName=$root_cn|ServerNameIndication=$sni|ErrorMessage=$error|ContainerID=$container_id|ContainerNameSpace=$pod_namespace|ContainerName=$pod_name|SourceEDL=$src_edl|DestinationEDL=$dst_edl|SourceDynamicAddressGroup=$src_dag|DestinationDynamicAddressGroup=$dst_dag|TimeGeneratedHighResolution=$high_res_timestamp|SourceDeviceCategory=$src_category|SourceDeviceProfile=$src_profile|SourceDeviceModel=$src_model|SourceDeviceVendor=$src_vendor|SourceDeviceOSFamily=$src_osfamily|SourceDeviceOSVersion=$src_osversion|SourceDeviceHost=$src_host|SourceDeviceMac=$src_mac|DestinationDeviceCategory=$dst_category|DestinationDeviceProfile=$dst_profile|DestinationDeviceModel=$dst_model|DestinationDeviceVendor=$dst_vendor|DestinationDeviceOSFamily=$dst_osfamily|DestinationDeviceOSVersion=$dst_osversion|DestinationDeviceHost=$dst_host|DestinationDeviceMac=$dst_mac|SequenceNo=$seqno|devTimeFormat=$cef-formatted-time_generated
¶ Log Forwarding Profile
On the Objects tab, navigate to Log Forwarding.
Create a new Log Forwarding Profile or edit an existing one, called “default”, and then configure each of the Log Types with the Syslog Profile created in the previous step.
TOP TIP: We recommend naming this profile “default”. When creating new rules, if a profile called “default” exists it will be automatically selected/prefilled. This eliminates the need to manually define it and reduces the risk of forgetting.
See screenshot below.
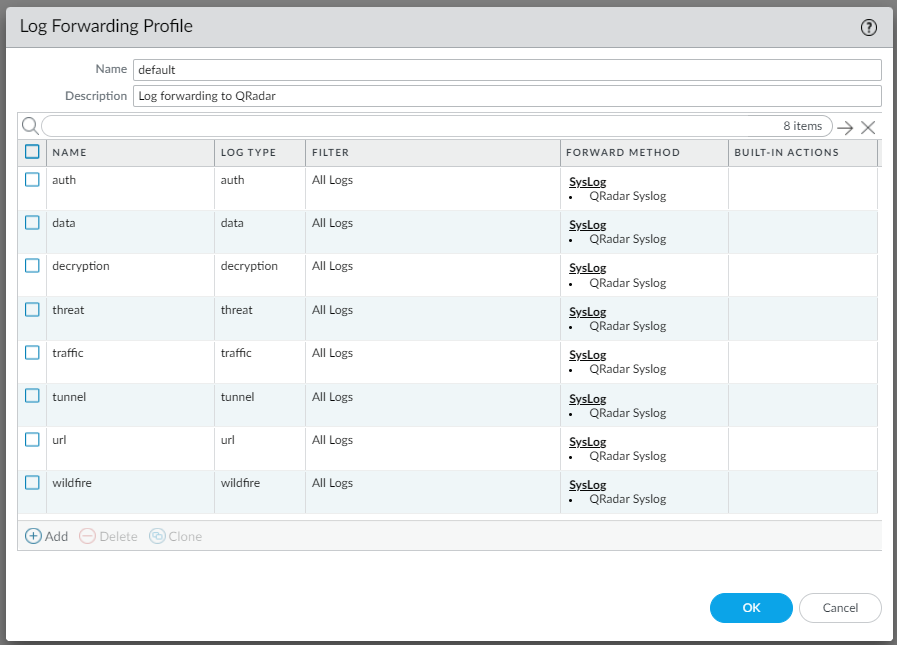
¶ Configuring Logs to be forwarded
¶ Forwarding Feature Specific Logs
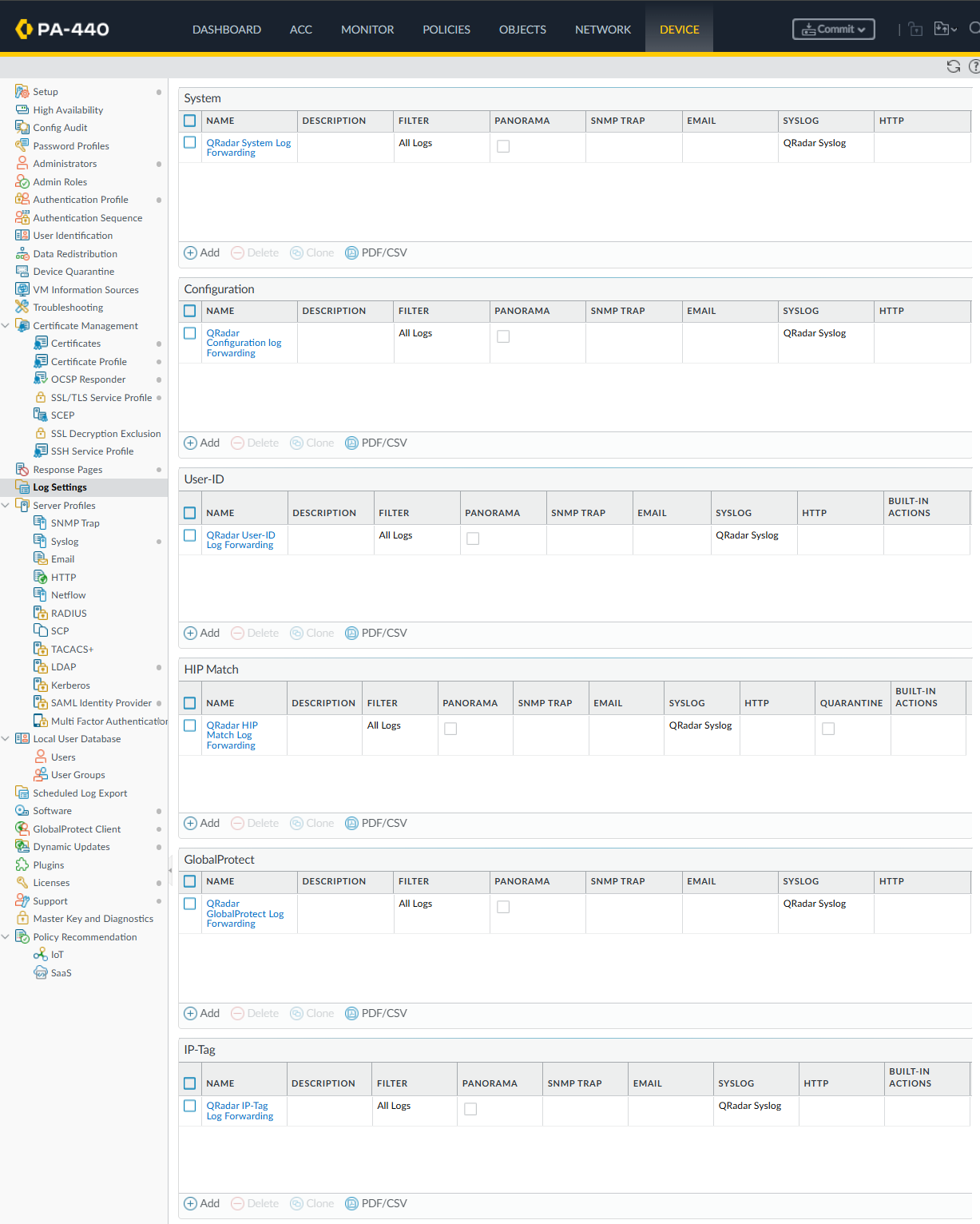
On the Device Tab, navigate to Log Settings
Configure all of the various Log forwarding/filtering options as per the below for the System, Configuration, User-ID, HIP Match, GlobalProtect and IP-Tag Logs.
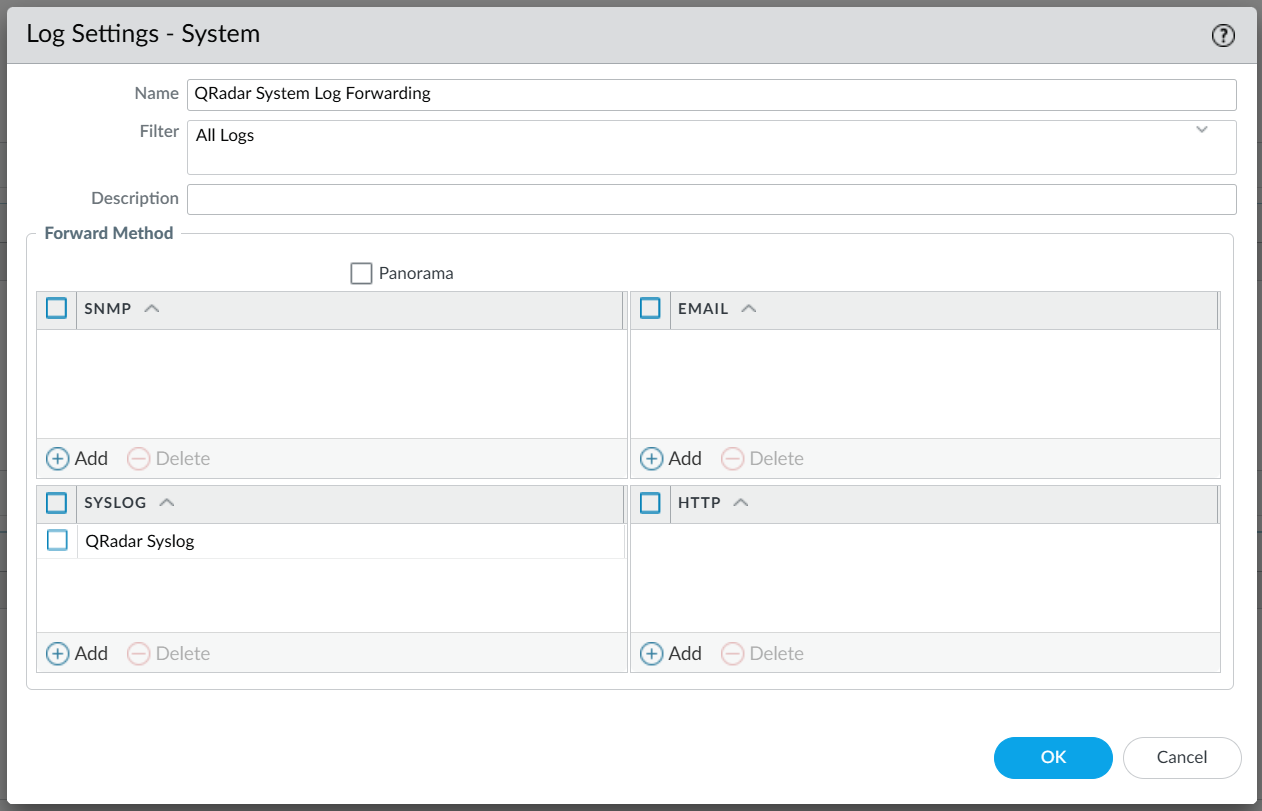
After configuring the log forwarding, your “Log Settings” configuration should look similiar to the below.
¶ Fowarding Traffic and Threat logs (Per Traffic Rule, Log Forwarding Profile selection)
Warning: If you do not assign the Log Forwarding Profile to your policies, only minimal logs will be sent.
Very few logs will be forwarded unless the newly created Log Forwarding Profile is defined in your Security/Authentication/DoS Protection/Tunnel Inspection policy rules, with the Security Policies being of the highest importance.
Review your rules, and apply the Log Forwarding Profile to any rules pertaining to Assets and Networks which fall under the scope of works of Secure-ISS’s Security Event Monitoring. If you have any doubt, please raise this with your onboarding contacts.
Firewall logs make up a sigficant amoumt of the volume of logs processed and stored, which may impact the anount of resources required to process and store them. However, Palo Alto logs provide a wealth of vital and detailed invalabule data and context so please take great care in ensuring you have applied log forwarding to all relevant rules that you currently have, and make going into the future.
This is why we recommend calling your Log Forwarding Profile “default” so it will automatically be selected when creating new rules.

